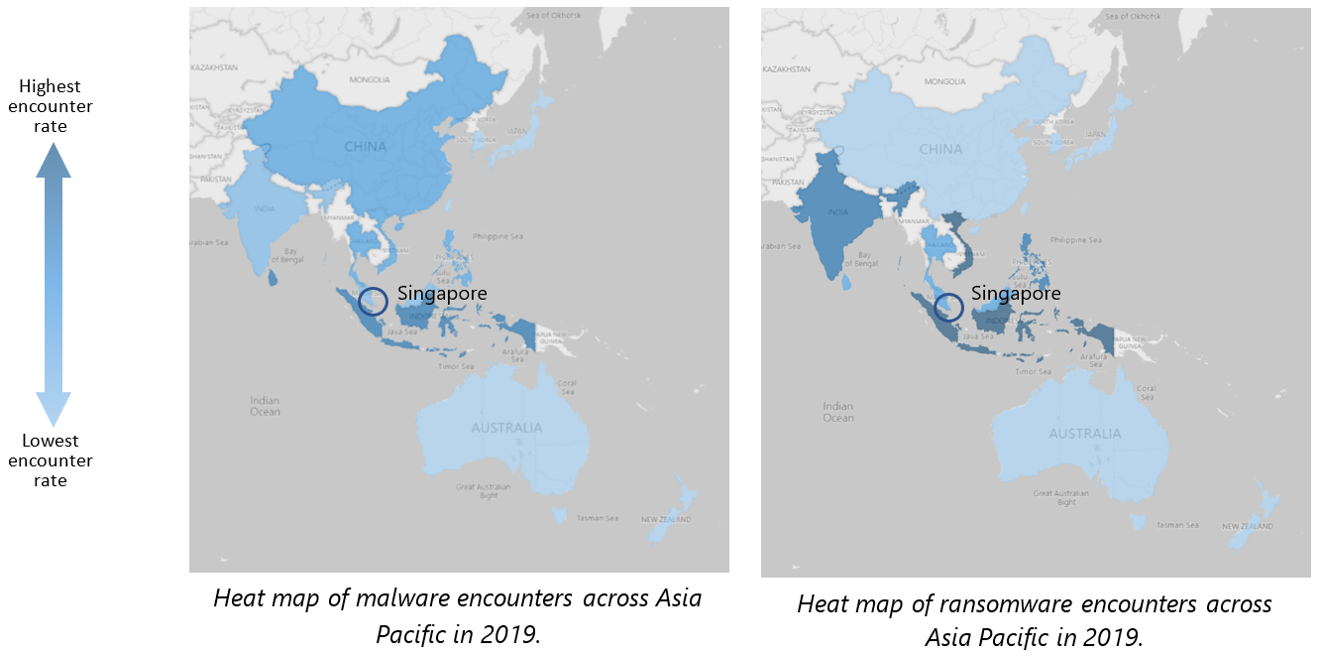
- Singapore tracked 138.5 percent increase in drive-by download attack volume in 2019 YoY.
- The country however recorded some of the lowest cryptocurrency mining, ransomware, and malware threat encounters across the region.
ASIA PACIFIC, SINGAPORE, 17 JUNE 2020 – Microsoft today unveiled Asia Pacific findings from the latest edition of its Security Endpoint Threat Report 2019[1], which placed Singapore among the countries with the highest drive-by download attack volume in the last year.
Findings were derived from an analysis of diverse Microsoft data sources, including eight trillion threat signals received and analyzed by the company every day, covering a 12-month period from January to December 2019.
“As security defenses evolve and attackers rely on new techniques, Microsoft’s unique access to billions of threat signals every day enables us to gather data and insights to inform our response to cyberattacks,” said Mary Jo Schrade, Assistant General Counsel, Microsoft Digital Crimes Unit, Microsoft Asia.
“The Microsoft Security Endpoint Threat report aims to create a better understanding of the evolving threat landscape and help organizations improve their cybersecurity posture by mitigating the effects of increasingly sophisticated attacks.”
Singapore registered one of the lowest malware and ransomware encounters
According to the report, Asia Pacific continues to experience a higher-than-average encounter rate for malware and ransomware attacks – 1.6 and 1.7 times higher than the rest of the world, respectively.
Singapore registered the fourth lowest malware (1.42 percent) and ransomware (0.01 percent) encounter rate in Asia Pacific after Japan, New Zealand and Australia. In the past year, the Republic saw a 49 percent and 67 percent decrease in its malware and ransomware encounter rate, respectively.
“Typically, high malware encounters are a result of excessive usage of unlicensed and/or pirated software, and proliferation of sites that illegitimately offer free software or content, such as video streaming. Consumer education is important – users should regularly patch and update programs and devices, and be able to identify illegitimate software,” explained Richard Koh, Chief Technology Officer, Microsoft Singapore.
Singapore’s cryptocurrency mining encounter rate was 5 times lower than the regional and global average
Singapore’s cryptocurrency mining encounter rate stood at 0.01 percent in 2019. This was an 80 percent decrease from 2018, and 5 times lower than the regional and global average of 0.05 percent, according to the report. The Asia Pacific region, in particular, saw a 64 percent decrease in its average encounter rate – mainly attributed to tightened regulations in developed countries like Hong Kong, Singapore, and Japan to counter malicious cryptocurrency crime.
During such attacks, victims’ computers are infected with cryptocurrency mining malware, allowing criminals to leverage the computing power of their computers to mine for cryptocurrency.
Cryptocurrency scams, coupled with relaxed regulatory implementations were key challenges in countries with high encounters, as this resulted in over the counter and fraudulent trading practices continuing to take place undetected.
“Improving user awareness is key in maintaining a low encounter rates and preventing consumers from falling for cryptocurrency scams. In Singapore particularly, strong government enforcement of cyber policies also helps ensure the efficacy of regulation on cryptocurrency trading and the integrity of cryptocurrency exchanges,” explained Koh.
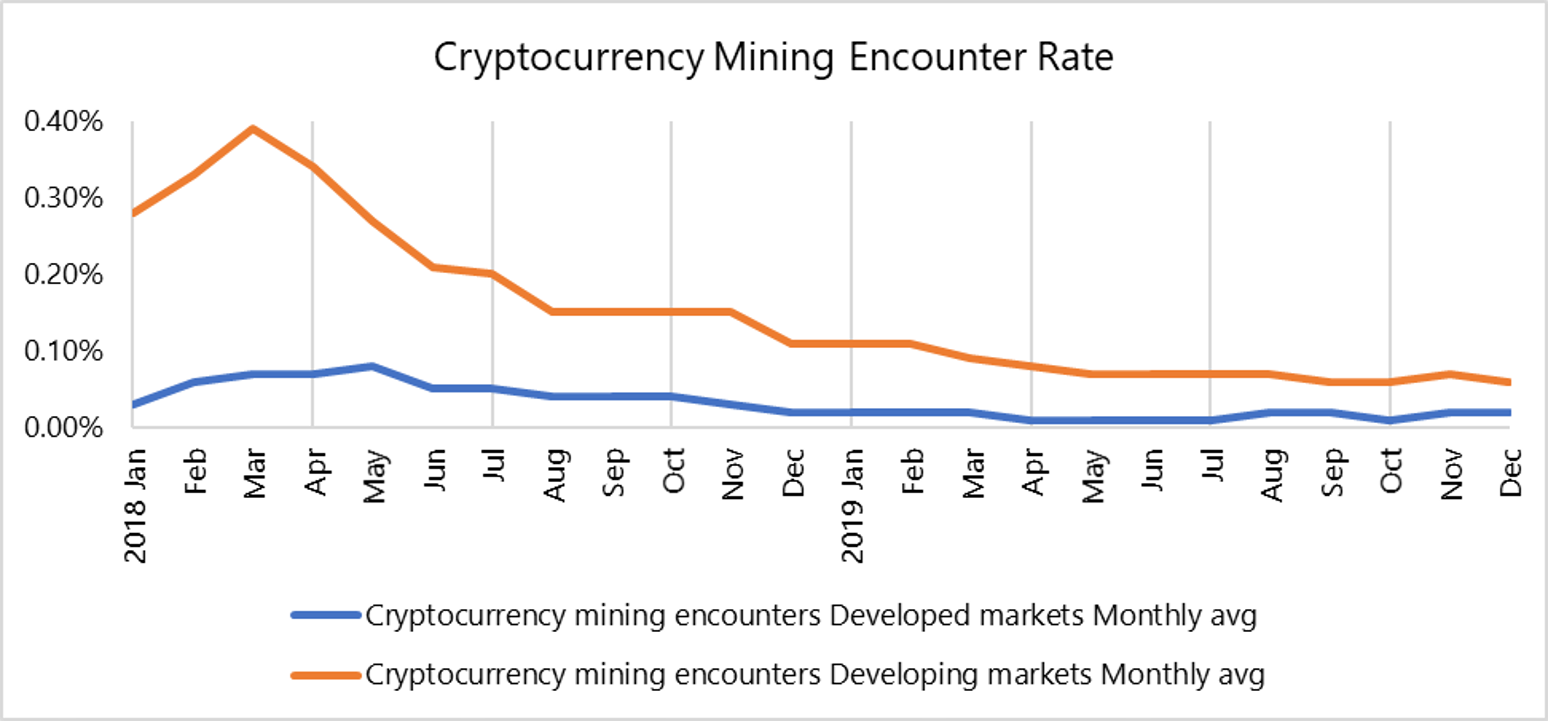
Comparison of cryptocurrency mining encounter rate across developed and developing markets in the region. According to the 2019 report, cryptocurrency scams continued to undermine cybersecurity levels in developing countries.
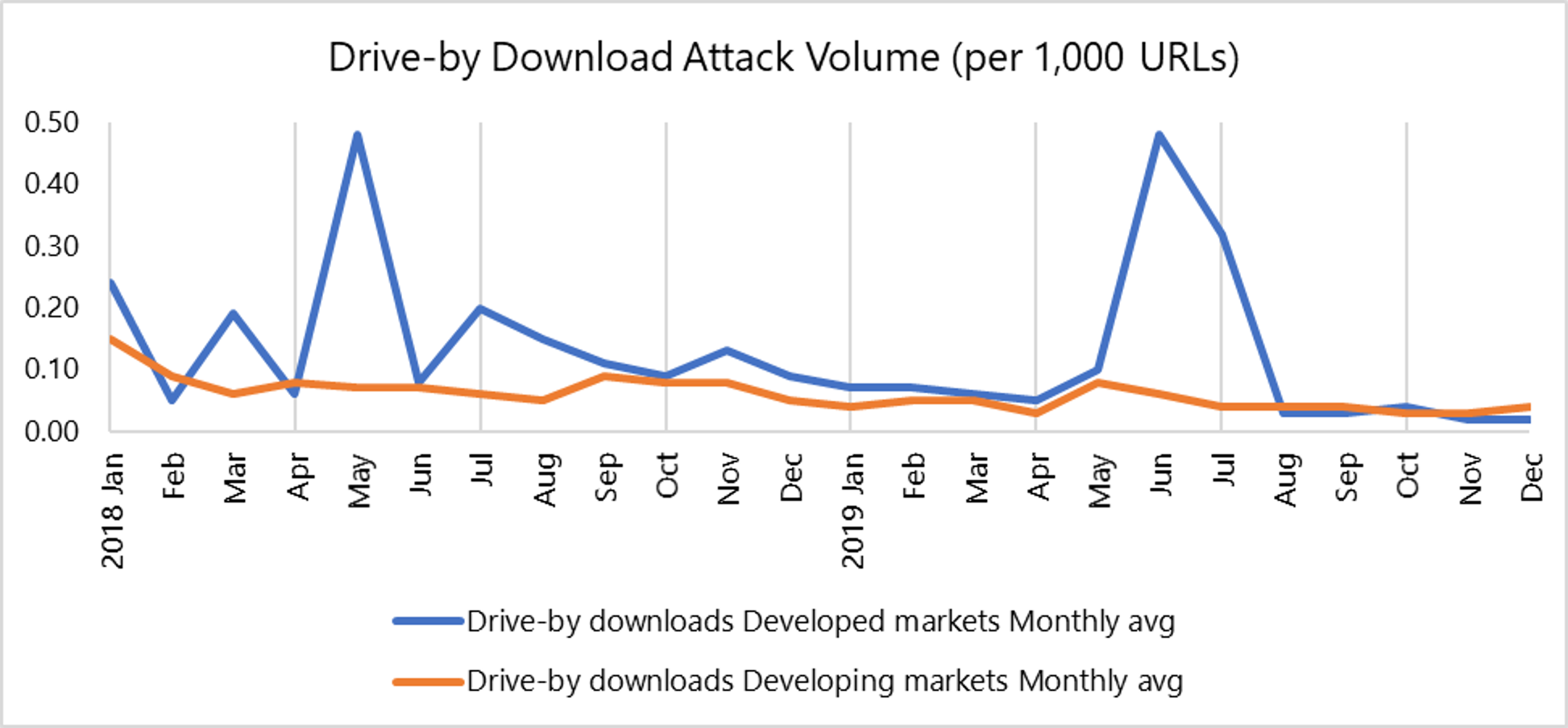
Singapore recorded the highest drive-by download attack volume in Asia Pacific
The drive-by download attack volume[2] in Asia Pacific has converged with the rest of the world at 0.08, following a 27 percent decline from 2018.
However, despite the general decline in drive-by download attacks across the region, the study found that Singapore experienced the highest attack volume of 0.31 in 2019 – an increase of 138.5 percent from 2018 (0.13). This was also 3.9 times higher than the 2019 global and regional average.
A similar trend was observed in Hong Kong and India, with both countries also recording an attack volume that was 3 times higher than the regional and global average.
These attacks involve downloading malicious code onto an unsuspecting user’s computer when the person visits a website or fills in a form. The malicious code that is downloaded can then be used by an attacker to steal passwords or financial information.
“Cybercriminals capitalize on drive-by download technique to target the organizations and end-users with the objective to steal valuable financial information or intellectual property. This is a likely reason for regional business hubs recording the highest volume of these threats,” explained Koh. “We’d like to emphasize that the high encounter rate does not necessarily translate into a high infection rate as the level of cyber hygiene and usage of genuine software prevents the systems from getting compromised.”
Comparison of drive-by download attacks across developed and developing markets in the region.
Cybersecurity in the age of COVID-19
With the turn of the new year, COVID-19 has changed the landscape and remains the top-of-mind concern for individuals, organizations, and governments around the world.
Since the outbreak, Microsoft Intelligence Protection team’s data has shown that every country in the world has seen at least one COVID-19 themed attack, and the volume of successful attacks in outbreak-hit countries seems to be increasing, as fear and the desire for information grows.
Of the millions of targeted phishing messages seen globally each day, roughly 60,000 include COVID-19 related malicious attachments or malicious URLs. Attackers are impersonating established entities like the World Health Organization (WHO), Centers for Disease Control and Prevention (CDC), and the Department of Health to get into inboxes.
Schrade further explained, “According to our data, we found that COVID-19 themed threats are mostly rethreads of existing attacks that have been slightly altered to tie to the pandemic. This means that attackers have been pivoting their existing infrastructure, like ransomware, phishing, and other malware delivery tools, to include COVID-19 keywords, to capitalize on people’s fear. Once users click on these malicious links, attackers can infiltrate networks, steal information and monetize their attacks.”
Businesses and individuals have a crucial role to play in navigating cyberspace securely and are encouraged to take the following steps:
Guidance for businesses:
- Have strong tools to safeguard employees and infrastructure. This means looking into multi-layered defense systems and turning on multi-factor authentication (MFA) as employees work from home. Additionally, enable endpoint protection and protect against shadow IT and unsanctioned app usage with solutions like Microsoft Cloud App Security
- Ensure employee guidelines are communicated clearly to employees. This includes information on how to identify phishing attempts, distinguishing between official communications and suspicious messages that violate company policy, and where these can be reported internally
- Choose a trusted application for audio/video calling and file sharing that ensures end-to-end encryption
Guidance for individuals:
- Update all devices with the latest security updates and use an antivirus or anti-malware service. For Windows 10 devices, Microsoft Defender Antivirus is a free built-in service enabled through settings
- Be alert to links and attachments, especially from unknown senders
- Use multi-factor authentication (MFA) on all accounts. Now, most online services provide a way to use your mobile device or other methods to protect your accounts in this way
- Get educated on how to recognize phishing attempts and report suspected encounters, including watching out for spelling and bad grammar, and suspicious links and attachments from people you do not know
For more information on the report findings, please visit: https://www.microsoft.com/securityinsights
[1] The research covered a total of 15 markets, which include China, India, Indonesia, Malaysia, Philippines, Sri Lanka, Thailand and Vietnam, Taiwan, Singapore, New Zealand, Korea, Japan, Hong Kong, and Australia.
[2] The Security Endpoint Threat Report records the average volume of drive-by download pages detected for every 1,000 pages indexed by Bing.