Jakarta, 10 December 2024 — Over the past twelve years, National Online Shopping Day (Harbolnas) 12.12 has become the most anticipated online shopping event in Indonesia. Last year, total transactions reached IDR 25.7 trillion, a significant increase from IDR 9.1 trillion in 2019. This year, the government aims for transactions to exceed IDR 29 trillion, highlighting the public’s enthusiasm for hunting online discounts*.
However, along with this spike in online transactions comes a heightened risk of cyber threats. According to the Microsoft Digital Defense Report 2024, threats such as phishing and Adversary-in-the-Middle (AiTM) attacks are becoming more sophisticated. In Indonesia alone, the National Cyber and Crypto Agency (BSSN) recorded over 102.95 million cyber traffic anomalies in the first half of 2024.
“During major events like Harbolnas 12.12, cybercriminals are likely preparing to launch more sophisticated attacks. Typically, they exploit shoppers’ urgency to complete transactions driven by deep discounts, limited product availability, and short-time offers, leading to a lack of verification of website or email authenticity,” said Panji Wasmana, National Technology Officer at Microsoft Indonesia. “Awareness and vigilance against cyber threats are crucial to preventing potential losses.”
Types of Cyber Threats Common During Harbolnas
One of the most common threats is phishing, a type of cyberattack designed to steal sensitive information by deceiving individuals. During Harbolnas 12.12, phishing attacks often occur when shoppers are directed to fake websites or bank accounts through promotional emails, text messages, phone calls, or QR codes. These sites mimic legitimate shopping platforms, tricking users into providing sensitive details such as credit card information and passwords. According to the Microsoft Digital Defense Report 2024, QR code phishing is now one of cybercriminals’ preferred methods.
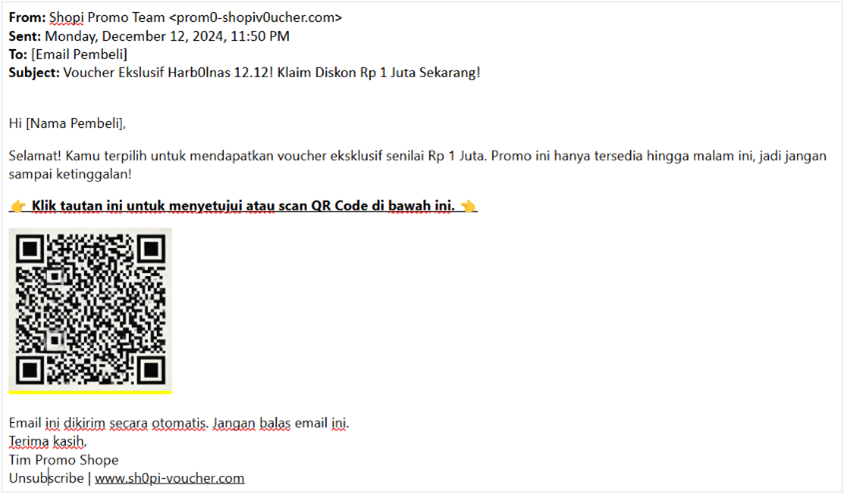
Another threat is tech scams. In tech scams, cybercriminals often contact users after they click on an advertisement or visit a shopping website, impersonating reputable companies to persuade them to share sensitive information or pay for fake services to “fix” non-existent problems. Microsoft reports show that tech scams cause significant financial losses globally—often up to ten times more than traditional phishing attacks. It is vital for users to remain vigilant and verify the authenticity of offers and websites.
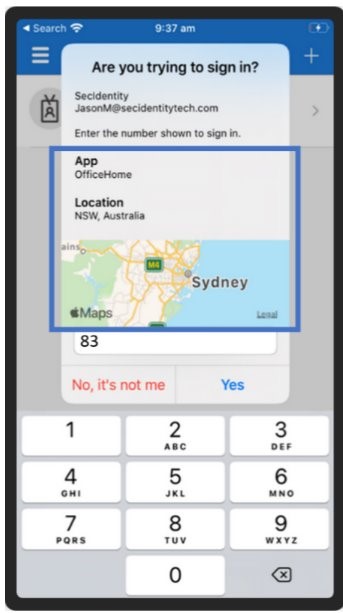
Another common threat is Adversary-in-the-Middle (AiTM) attacks, a technique where attackers insert themselves between a user and a legitimate authentication service. This method often utilizes what is referred to as “Multi-Factor Authentication (MFA) fatigue,” where perpetrators bombard users with repeated fake authentication requests, hoping the user—distracted by the excitement of discounts—accidentally approves a fraudulent login attempt.
Tips for a Safer Shopping During Harbolnas 12.12
Understanding these threats, Microsoft shares tips to enhance security while shopping online:
- Don’t rush to click links, open attachments, or make payments without double-checking: Always verify links and attachments in promotional emails or discount offers. Check the retailer’s official website and social media channels to confirm authenticity. Watch for fake communications with suspicious domain names or other anomalies.
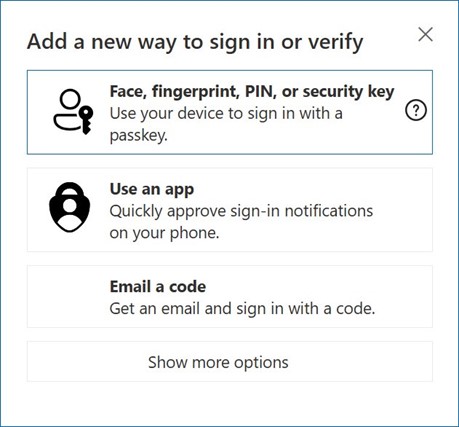
- Use stronger authentication: Consider using a password manager to create and store unique passwords securely. Whenever possible, activate MFA for an additional layer of security. MFA can block 99% of password-based attacks, according to the Microsoft Digital Defense Report. Additionally, use passkeys—private digital keys protected by biometric data (such as facial recognition or fingerprints) or a PIN—when the device, website, and app allow it. These keys only work with the site or app where they were created and are accessible exclusively to the user by unlocking it with their biometrics information or PIN.
- Secure your device with the latest updates and patches: Regularly update your devices and applications, both desktop and mobile. Avoid conducting financial transactions over public Wi-Fi.
###
* Director General of Domestic Trade at the Ministry of Trade (Kemendag), as quoted by CNBCIndonesia.com

