Ome Sivadith
National Technology Officer
Microsoft (Thailand) Limited
Over the past year, we have seen vast changes around us. Work is no longer confined to the office and now transcends physical locations, leading us to communicate digitally more and more. We have entered an era of hybrid work where technology plays a massive role, and this shift has a direct impact on how we must approach cybersecurity. An organization’s systems no longer exist just for its employees but also partners, customers, or even automated bots. Devices and applications are scattered far and wide – from personal computers and smartphones owned by employees and external chat applications to IoT equipment and cloud-based apps. As a result, we now have a level of agility that lets us compete better and respond faster to new opportunities.
With the organization’s technologies spread across more endpoints, its network similarly no longer covers just the premises of its offices – and there are many more areas and factors to protect. Cybersecurity in this day and age requires what we call “Zero Trust” – an approach to threat prevention that has long driven Microsoft’s work in this area and elevated our capabilities to match escalating threats.
The Zero Trust approach is something that every organization can adopt – not just Microsoft. However, the process of adoption always starts with one key question: “Where and how should we start?”
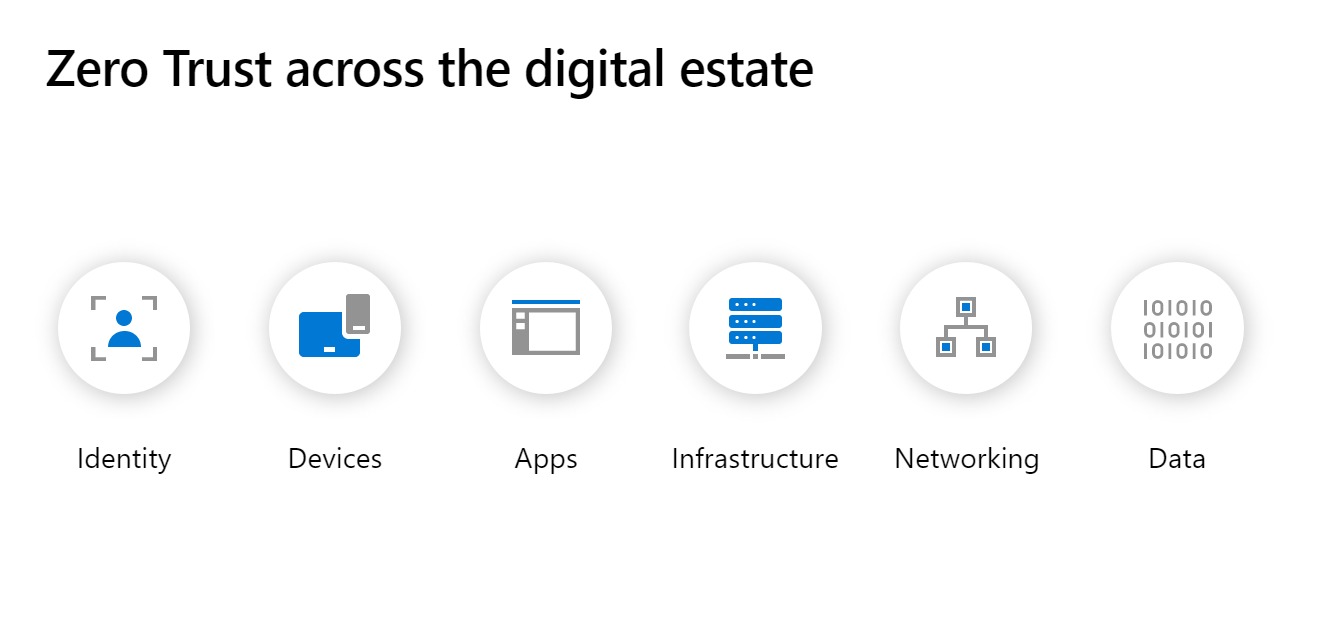
At Microsoft, we break Zero Trust down into six key components across an organization’s digital estate:
- Identity – Verifying that a user is genuine
- Device – Protecting endpoints such as computers or smartphones
- Apps – All the apps in use within the organization
- Infrastructure – Hardware and software in place across the organization
- Networking – Networks spread throughout the organization
- Data – All data stored and processed by the organization
While infrastructure and networking are standout priorities for many, a Microsoft survey last year in the US and Canada found that 38% of IT executives see devices as top priority, while 24% chose identity as their most important factor. While 79% of organizations are confident in achieving a Zero Trust environment for devices, only 52% feel the same way when it comes to securing user identities1 – even though these two aspects are highly intertwined and securing both in parallel is highly advisable.
Reinforcing security in any of these six aspects is no easy task as each has its own share of intricacies – but for identity and devices, there are a few basic concepts that every organization can implement.
- Verify explicitly – even with your own employees. Unusually access attempts from strange locations, new devices, or even an odd time of day may be signs of a malicious actor at work with stolen credentials or devices. Of course, every device must be kept safe and clean from malware and other threats.
- Grant only minimum necessary access. No individual user needs access to every last piece of data in the organization, so provide access to only what is needed to accomplish the task at hand. In addition to preventing confusion, this limits the risk of leaks as well.
- Assume a breach at any time to minimize potential damage. Leaving damage limitation and defensive measures until an attack has been detected would be far too late. A truly effective defense requires the security systems that can detect suspicious signals of an impending attack in advance.
These three basic steps serve as a good start for any organization embarking on a Zero Trust journey. Of course, a truly secure Zero Trust environment cannot be achieved by skipping over any of the six key aspects, and the remaining four should be milestones to aim for.
For a more in-depth look at cybersecurity – including changes required to ensure compliance under the Personal Data Protection Act ahead of its full enforcement – find out more in Microsoft’s free e-book by registering here.