Microsoft released the third edition of Cyber Signals report, spotlighting security trends and insights gathered from Microsoft’s 43 trillion daily security signals and 8,500 security experts. The content offers an expert perspective into the current threat landscape, highlighting recent trends, attacks, and strategies as well as practical recommendations for enterprises.
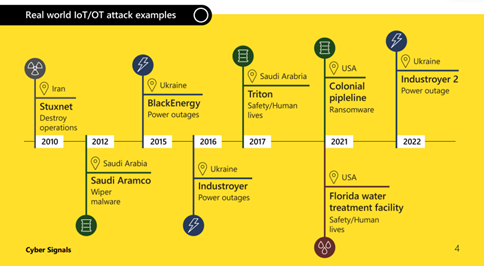
Internet-of-Things* and Operational Technology (OT) devices** are rapidly expanding and converge to support business needs in different industries. But their rapid increase creates an expanded entry point for attackers. Thus, over the past year, the corporation has observed threats exploiting devices in almost every part of an organization. With more than 41 billion IoT devices across enterprise and consumer environments expected by 2025 — according to International Data Corporation research — devices such as cameras, smart speakers, or locks and commercial appliances can become entry points for attackers.
Although security of IT equipment has strengthened in recent years, IoT and OT device security has not kept pace. Attackers can have varied motives to compromise devices other than typical laptops and smartphones.
So establishing a more secure relationship between IT and OT require consideration of control measures. Air-gapped devices and perimeter security are no longer sufficient to address and defend against modern threats like sophisticated malware, targeted attacks, and malicious insiders, attackers also abuse of employee login credentials or exploitation of access granted to third-party suppliers and contractors to the networks.
An example of a malware incident was a case of a major global food and beverage company using very old operating systems to manage factory operations. In 2022 Microsoft assisted to repel an attack while performing routine maintenance on equipment that would later connect to the Internet, malware spread to factory systems via a compromised contractor laptop. While an ICS environment can be isolated from the Internet, the moment a compromised laptop is connected to a formerly secure OT device or network it becomes vulnerable. Across the customer networks Microsoft monitors, 29% of Windows operating systems have versions that are no longer supported.
A defense based on Zero Trust, effective policy enforcement, and continuous monitoring can help prevent or contain incidents like this in cloud connected environments. Microsoft released an open source forensics tool to the defender community, to help incident responders and security specialists better understand their environments and investigate potential incidents.
We are in a connected age, there’s an expectation that everything should be connected to provide a real-time experience enabling OT data to flow to the cloud. This provides more valuable data analytics, automation and efficiency enterprises previously were unable achieve. However, the overwhelming speed of these devices’ connected evolution, and organizations’ incomplete inventory and visibility of them, often tilt the playing field to attackers. Almost every attack we’ve seen in the last year started from initial access to an IT network that was leveraged into the OT environment.
Critical infrastructure security is a worldwide challenge and to face with it the corporation recommends:
- Work with stakeholders: Map business-critical assets, in IT and OT environments.
- Device visibility: Identify what IoT and OT devices are critical assets by themselves, and which are associated with other critical assets.
- Perform a risk analysis on critical assets: Focus on the business impact of different attack scenarios as suggested by MITRE.
- Define a strategy: Address the risks identified, driving priority from business impact.
- Implement new and improved policies: Policies stemming from the Zero Trust methodology and best practices provide a holistic approach for enabling seamless security and governance across all your devices.
- Adopt a comprehensive and dedicated security solution: Enable visibility, continuous monitoring, attack surface assessment, threat detection, and response.
- Educate and train: Security teams require training specific to threats originating from or targeting IoT/OT systems.
- Examine means of augmenting existing security operations: Address IoT and OT security concerns to achieve a unified IT and OT/IoT SOC across all environments.
Microsoft will invest $20 billion over the next five years to accelerate efforts to integrate cyber security by design and to deliver advanced security solutions. This includes $150 million in technical services to help federal, state, and local governments upgrade security protection and help ensure they deploy the best and most up to date security tools available. The attacks show that no organization is immune to the threat posed by well-funded and determined adversaries and defending against cybercriminals is a complex, ever evolving, and never-ending challenge. Protecting the internet requires policymakers, the business community, government agencies and, ultimately, individuals to make a real difference, and we can only have significant impact through shared information and partnerships.
To find out more, check video interview between Ratko Mutavdžić, CEMA Government Lead in Microsoft and Dragan Petric, Executive Editor of Bug magazine:
*IoT is a system of interrelated computing devices and objects, that are provided the ability to transfer data over a network
**OT devices – hardware and software that detects or causes a change, through the direct monitoring and/or control of industrial equipment, assets, processes, and events.





