Universities, one of the most popular targets for cybercriminals, are employing a new tool in the fight against cybercrime – their own students.
Over the past few years, universities and colleges around the U.S. have been increasingly hiring students and training them to become analysts in their security operations centers, known as SOCs. Students work alongside full-time employees on tasks like reviewing incident reports, hunting for cyberthreats and investigating suspicious online behavior. The centers are typically located on campus, though some employees work remotely, and staffing is arranged around students’ academic schedules.
The model offers benefits on both sides: Students get valuable hands-on experience defending a large organization against cyberattacks, and universities get IT resources at a lower cost while addressing a cybersecurity workforce shortage.

“It’s really cool for a student to be able to say, ‘I’m actually doing real SOC analyst work,” says David McMorries, chief information security officer at Oregon State University, whose SOC employs around eight students.
“We’re giving people who have huge enthusiasm, but not a lot of experience, the ability to get experience. And that makes them super marketable when they leave.”
That was the case for George Cothren, who began working at the SOC at Auburn University in Alabama as a 19-year-old freshman. He knew little about cybersecurity at the time, other than “you don’t want other people getting your password,” and figured he wouldn’t get hired. But he did.

Cothren worked at the SOC for three years until graduating, handling tasks including threat detection, responding to email incidents and supporting efforts to roll out the Microsoft Defender for Endpoint security platform campuswide. He worked closely with the university’s external security consultants and earned several cybersecurity certifications.
Two weeks after graduating with a computer science degree in 2024, Cothren started a position as a senior cybersecurity analyst at Regions Bank, a job he says his SOC experience “absolutely” helped him get.
“Companies really don’t look for students fresh out of college, because cybersecurity is about protecting billion-dollar corporations – their data, their reputation, their integrity,” says Cothren, now 23. “I am very lucky for having had three years of experience.”

A student-fueled solution
Student-assisted SOCs have become more prevalent over the past five years, coinciding with a dramatic increase in cyberattacks against colleges and universities. The education sector is now the third most targeted industry for cybercrime globally, a recent Microsoft report found, and universities face unique cybersecurity challenges.
University culture values openness and information-sharing, but universities also must protect intellectual property and highly sensitive data on staff and students, typically with small IT departments and funding constraints.
In 2019, Jay James was looking to build out the SOC at Auburn University. The university’s senior cybersecurity operations lead, James quickly realized that even if Auburn had the resources to hire professional analysts, with more than 400,000 unfilled cybersecurity jobs in the U.S., it would be tough to fill those roles.
Student analysts at university SOCs typically make around $15 to $25 hourly, according to Microsoft, compared with an average starting salary of around $99,000 to $122,000 – generally more than $45 hourly – for a cybersecurity analyst in the U.S.

James came up with a solution – he’d hire students. He initially hired two students to work in the SOC, eventually expanding to around 10.
On a typical day, student SOC employees triage incidents captured by the Microsoft Defender XDR platform – anything from malware on a laptop to suspicious activity on a student’s email account – look for potential online threats and work on their own cybersecurity projects. More serious incidents are escalated up to the SOC’s full-time staff.
As additional support to full-time employees, students also help uncover vulnerabilities. One student analyst, James says, discovered an issue with a camera on campus that created a potential security risk but was easily fixable.
“As a higher-ed institution, our No. 1 priority is empowering students for whatever they plan on doing next,” he says. “It’s a win where the students have the opportunity to get hands-on experience and we’re able to utilize those students to help secure the university.”

At the University of Tennessee, Knoxville, the SOC’s student employees have uncovered what Chief Information Security and Technology Officer Matthew Williams calls “slow burn” issues, seemingly random low-priority incidents that when grouped together point to an emerging problem. Before employing students at the SOC, Williams says, that type of analysis didn’t happen.
“We unfortunately just used to look at alerts in isolation because of staffing,” he says. “Now we have the resources to look at things at more of a high level and in aggregate that could point to issues that we have otherwise just not paid attention to.”
‘A game-changer’
Oregon State University was ahead of the curve when it began hiring students at its SOC around 2015. Things hummed along nicely until 2021, when the university experienced a serious cybersecurity incident that appeared to be the precursor to a ransomware attack.
OSU moved quickly to implement technologies including Microsoft Sentinel and Microsoft Defender and hire additional SOC staff, with Microsoft providing coaching and mentoring. The university, McMorries says, now has a robust team of student SOC employees and greater visibility into its cybersecurity operations. Around 80% of its security incidents are resolved through automation.
“Our ability to react and respond to things is so much better than it was four years ago,” McMorries says.
He attributes that in part to Microsoft Security Copilot, a generative AI tool launched in April 2024 that uses natural language to assist with cybersecurity tasks and turn data into insights. Security Copilot empowers junior analysts, allowing them to take on entry-level tasks with expert-level confidence.
Copilot provides summaries of cybersecurity incidents, McMorries says, helping new student SOC employees learn and making it easier to hire students without computer science backgrounds.
“It lowers the barriers for students who have some aptitude or interest in cybersecurity and could do well,” he says.
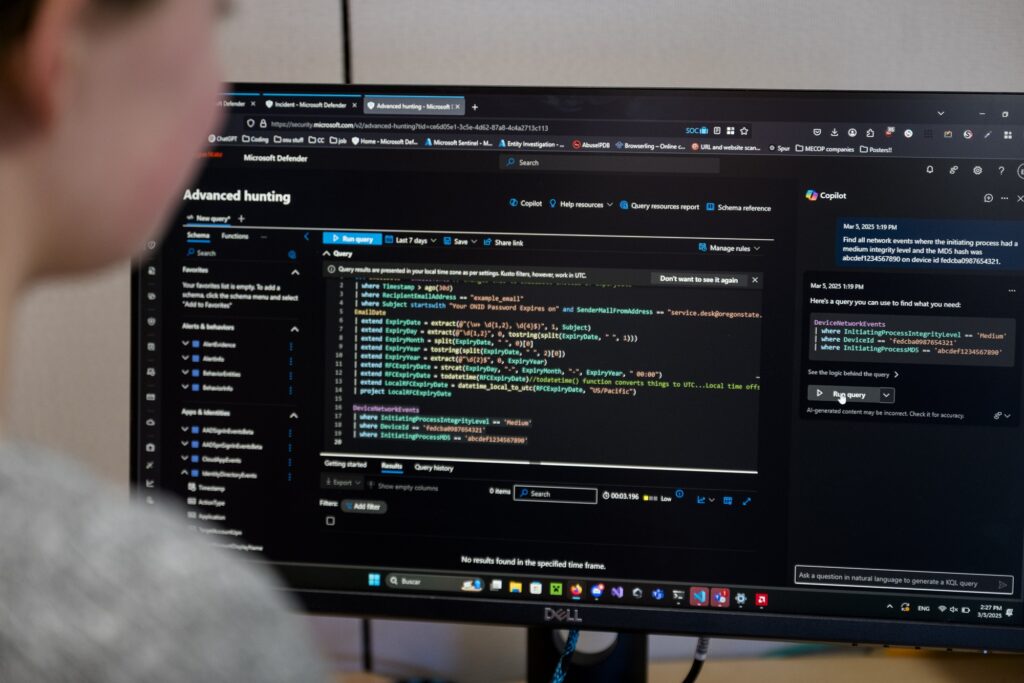
Security Copilot can also develop queries to search for particular threats in the university’s environment, McMorries says. Additionally, he says, SOC employees often use Security Copilot to help write queries in KQL, the language used for many Microsoft services, without them needing to learn it.
“It’s very powerful and speeds up the SOC in the way it operates,” McMorries says. “It gets students up to speed quicker, and it puts in one pane of glass the ability to pull in information that you might otherwise have to chase around a lot of other places to find.”
James says Security Copilot is “almost like training wheels” for Auburn University’s new student SOC analysts, coaching them through tasks, and is also a time-saver for more experienced employees.
“If I want more context around a particular incident, I can just ask Copilot and it gives me all of the context,” James says. “It helps us triage faster, find things out faster and assists us in ways that would otherwise take multiple FTEs to do.
“It is definitely a game-changer.”

Corey Lee, a Microsoft security chief technology officer who provides training and support to educational organization SOCs, says generative AI can transform cybersecurity by using conversational language to break down complex issues, providing prompts for queries and automating time-consuming tasks.
“This is what we want the industry to shift to – not doing all the drudgery and the busy work, but getting to more proactive security work,” he says.
“That is what AI is bringing to the table. It’s going to democratize access to advanced levels of security expertise and knowledge.”
Tackling the gender gap
Beyond providing hands-on experience and filling IT jobs, student-powered SOCs could offer another benefit – helping reduce the cybersecurity gender gap. Women comprise only around 19% of the U.S.’s cybersecurity workforce, a recent study found, and that disparity has remained stubbornly constant.
In 2015, Emily Longman was the first woman hired at Oregon State University’s SOC, after Dave Nevin, OSU’s former chief information security officer, encouraged her to apply. For eight years, Longman remained the SOC’s only female employee, despite what she deems the university’s “excellent commitment” to inclusive hiring practices.
“I’m always sad when we have hiring pools and there’s like two female applicants and 40 male applicants,” says Longman, now the manager of the university’s SOC.

Longman set out to change that, going to meetings of OSU’s cybersecurity clubs and encouraging women to apply at the SOC. She hired Grace Parrish and Emily MacPherson, computer science students who have been working at the SOC since July 2023 and October 2024, respectively.
Parrish got interested in hacking Wi-Fi encryption when she was in high school, studied mechatronics and returned to college in her 30s to study cybersecurity. The SOC, she says, has given her valuable experience in creating efficiencies through automation and working with teammates to defend the university against cyberattacks.
“I like getting to put my hands on some nice enterprise-grade security solutions,” says Parrish, an OSU senior who co-founded the university’s WiCys club for women in cybersecurity.
“And I really enjoy working on automation projects. They’re like little puzzles to me.”

MacPherson’s interest in cybersecurity was piqued as a child by seeing hackers in movies, and by middle school classmates who figured out how to get around computer filters to play video games. A cybersecurity class in high school, where she learned about cryptography and wrote a program that successfully broke an encryption method, cemented her passion.
“Doing that, I had so much fun,” says MacPherson, a sophomore at OSU. “It was like the joy of my life.”
Working at the SOC, she says, has taught her about attacker strategies and internet mechanisms and improved her problem-solving skills. Like Parrish, she plans to pursue a career in cybersecurity. But for now, MacPherson is finding satisfaction in helping protect her university community against cyberattacks.
“I am helping, even if it’s just in a small way, to protect OSU and defend our network from malicious attackers,” she says. “Just knowing I’m part of that is really cool.”
Top photo: Student Grace Parrish, left, who works at Oregon State University’s security operations center, talks with SOC manager Emily Longman. Photos by Karl Maasdam for Microsoft unless otherwise noted.


