Microsoft published the fourth annual Microsoft Digital Defense Report, which covers trends between July 2022 and June 2023 across nation-state activity, cybercrime, and defense techniques. Microsoft’s Threat Intelligence tracked more than 300 unique threat actors. 100.000+ domains utilized by cybercriminals have been removed. user password attacks have increased tenfold in the past year, with Microsoft having observed approximately 6,000 MFA fatigue attempts per day over the last year.
Cyberattacks have touched 120 countries in the past year, fueled by government-sponsored spying and with influence operations (IO) also rising. At times, nearly half of these attacks targeted NATO member states, and more than 40% were leveled against government or private-sector organizations involved in building and maintaining critical infrastructure. While attacks from the past year were often focused on destruction or financial gain with ransomware, data shows the predominant motivation has swung back to a desire to steal information, covertly monitor communication, or to manipulate what people read.

Multifactor Authentication (MFA) fatigue attacks increased by ten times
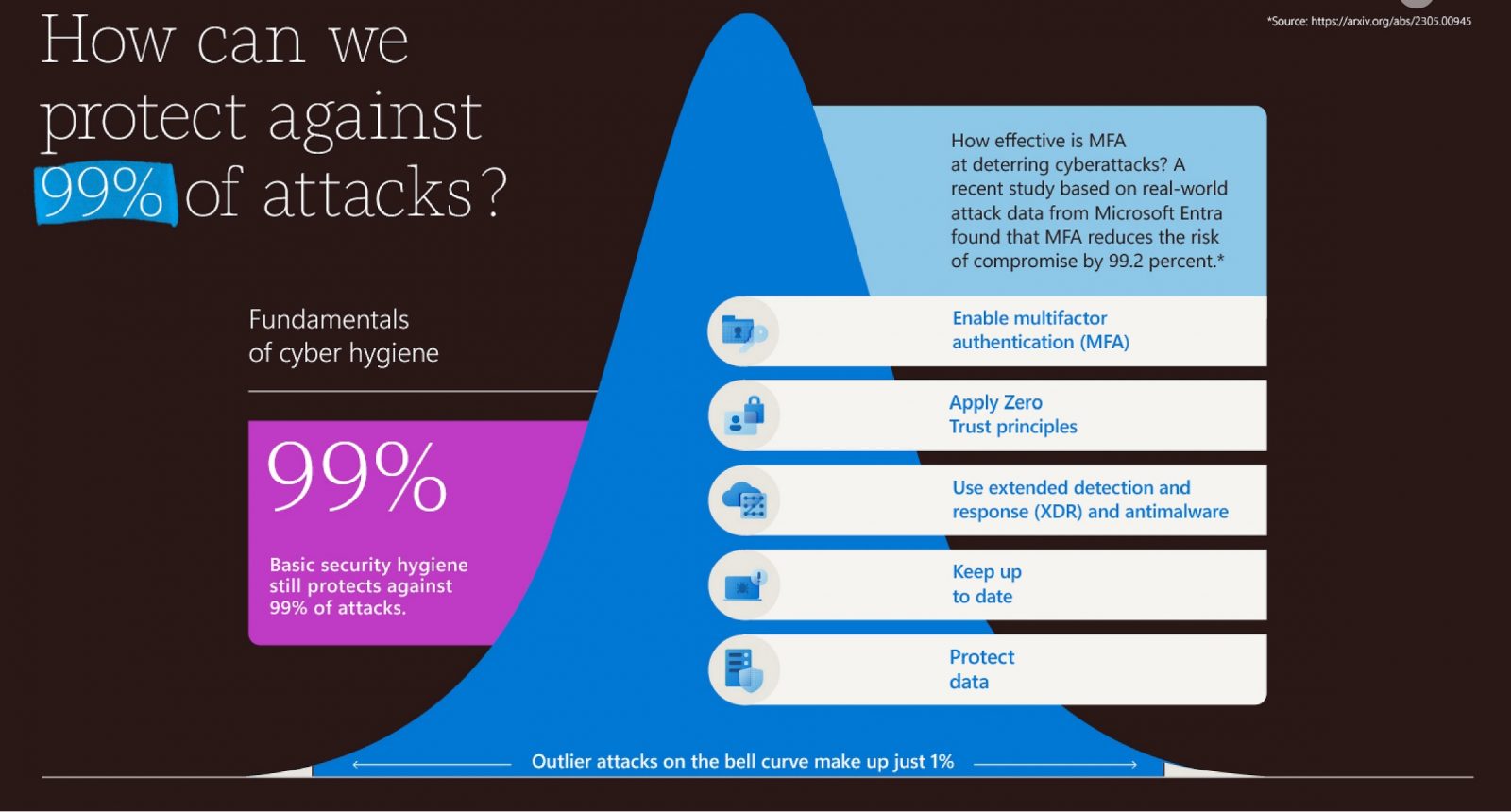
MFA is the increasingly common authentication method that requires users to provide two or more “factors” of identification to gain access to a website or application – such as a password along with facial recognition or a one-time passcode. While deploying MFA reduces the risk of compromise by 99.2%, threat actors are increasingly taking advantage of “MFA fatigue” to bombard users with MFA notifications in the hope they will finally accept and provide access.
Microsoft has observed approximately 6,000 MFA fatigue attempts per day over the past year. The first quarter of 2023 saw a dramatic tenfold surge in password-based attacks against cloud identities, from around 3 billion per month to over 30 billion.
“We see a disturbing trend of increasing cybercrime. For example, user password attacks have increased tenfold in the past year, with an average of 4,000 attacks per second. Microsoft and other technology companies continue to innovate security measures to protect users at the individual, company, and state levels,” says Onur Koc, National Technology Officer at Microsoft.
More countries, sectors under attack
While the U.S., Ukraine, and Israel continue to be most heavily attacked, the last year has seen an increase in the global scope of attacks. Iran increased its operations in the Middle East. Organizations involved in policymaking and execution were among the most targeted, in line with the shift in focus to espionage.
Nation state actors are more frequently employing influence operations (IO) alongside cyber operations to spread favored propaganda narratives. For example, following its invasion of Ukraine, Russia consistently timed its IO operations with military and cyberattacks. Similarly, in July and September 2022, Iran followed destructive cyberattacks on the Albanian government with a coordinated influence campaign which is still ongoing.
Both Russia and China are increasing the scope of their influence operations against a variety of diasporas. Russia aims to intimidate global Ukrainian communities and sow mistrust between war refugees and host communities in a range of countries, especially Poland and the Baltic states. Russian state actors expanded their Ukraine-related activities to target Kyiv’s allies, principally NATO members. In April and May 2023, Microsoft observed a spike in activity against Western organizations, 46% of which were in NATO member states, particularly the United States, the United Kingdom, and Poland. China’s expanded and sophisticated activities reflect its dual pursuits of global influence and intelligence collection. Their targets are most commonly U.S. defense and critical infrastructure, nations bordering the South China Sea (especially Taiwan) and even China’s own strategic partners. The past year has seen some Iranian state actors increase the complexity of their attacks. North Korea has increased the sophistication of its cyber operations in the last year, especially in cryptocurrency theft and supply-chain attacks. Additionally, North Korea is using spear-phishing emails and LinkedIn profiles to target Korean peninsula experts around the world to gather intelligence.
AI creates new threats – and new opportunities for defense
Attackers are already using AI as a weapon to refine phishing messages and improve influence operations with synthetic imagery. But AI will also be crucial for successful defense, automating, and augmenting aspects of cybersecurity such as threat detection, response, analysis, and prediction. AI can also enable large language models (LLMs) to generate natural language insights and recommendations from complex data, helping make analysts more effective and responsive. We are already seeing AI-powered cyber-defense reversing the tide of cyberattacks; in Ukraine, for example, AI has helped defend against Russia.
The state of cybercrime
While threat groups have significantly accelerated the pace of their attacks over the last year, built-in protections across Microsoft products have blocked tens of billions of malware threats, thwarted 237 billion brute-force password attack attempts, and mitigated 619,000 distributed denial of service (DDoS) attacks that aim to disable a server, service, or network by overwhelming it with a flood of internet traffic.
Ransomware attacks increase in sophistication and speed
Microsoft’s telemetry indicates organizations saw human-operated ransomware attacks increase 200% since September 2022. These attacks are generally targeted attacks pointed at a whole organization with ransom demands. Attackers are also evolving attacks to minimize their footprint, with 60% using remote encryption, thereby rendering process-based remediation ineffective. These attacks are also notable for how they attempt to gain access to unmanaged or bring-your-own devices. More than 80% of all compromises Microsoft observed originate from such unmanaged devices.
Basic security hygiene still protects from 98% of attacks. Resilience success factors every organization should adopt are to enable multifactor authentication (MFA), to apply Zero Trust principles, to use extended detection and response anti-malware, to keep systems up to date, and to protect data.





