Asia’s emerging economies are among the world’s most vulnerable and exposed to malware and other cyber threats, a new report says.
Regional findings from Microsoft’s global Security Intelligence Report (SIR), volume 22, put Bangladesh and Pakistan at the top the global at-risk list. In contrast, Japan is the least at-risk nation.
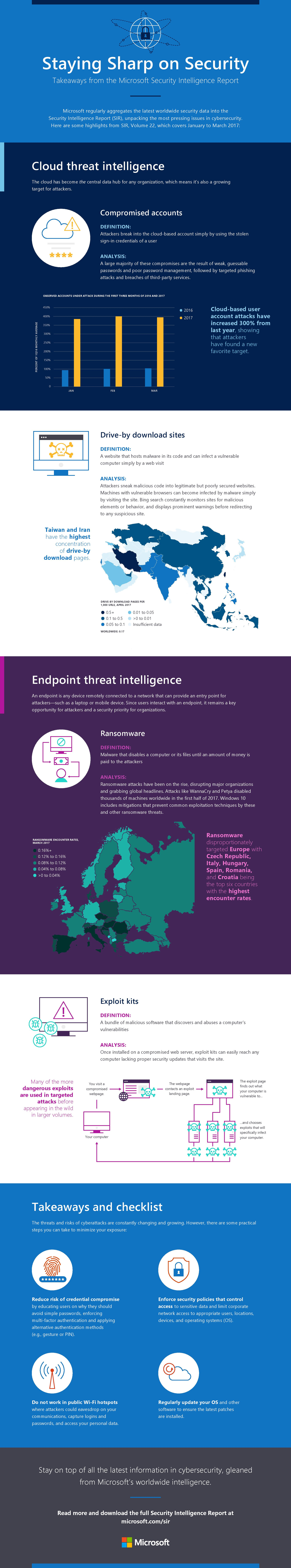
The global report, which covers the first three months of this year, provides in-depth data and insights into the global threat landscape, particularly in software vulnerabilities, exploits, malware, and web-based attacks. It tracks endpoint as well as cloud threat data and profiles of more than 100 individual markets. It also shares best practices and solutions that can help organizations better protect, detect and respond to threats.
“Driven by the proliferation of endpoints and the ubiquitous computing power of the cloud, the opportunity for digital transformation to make broad and profound impacts across our society has never been greater,” said Keshav Dhakad, Assistant General Counsel and Regional Director, Digital Crimes Unit (DCU), Microsoft Asia. “However, for digitalization to reach its fullest potential, users must first trust the technology they use.
“Microsoft is committed to helping our customers and partners build that trust and the first step is to help them understand the multitude of cyber threats out there so that they can implement more effective ways to manage and neutralize these risks.”
ALSO READ: Cyber Trust Experience 2017: Empowering individuals and organizations to achieve more with trust
Behind Bangladesh and Pakistan, the other most at-risk countries were Cambodia and Indonesia. Approximately one in four computers running Microsoft real-time security products in these countries reported a malware encounter from January to March 2017.
Other nations facing the biggest malware threats include Myanmar, Nepal, Thailand, and Vietnam. Each had an average malware encounter rate of more than 20 percent in the first quarter.
This is more than double the global average of nine percent. Taiwan also had a high concentration of drive-by download pages that host malware in its code and can infect a vulnerable computer simply by a web visit.
In contrast, markets with higher levels of IT maturity – namely Australia, Hong Kong, Japan, New Zealand, and Singapore – performed better than the worldwide average.
Japan has been ranked the safest country in the world, with only two percent of its computers reporting a malicious program incident.
Malware Encounter Rates for Markets in Asia in Q1 2017 (from most at risk to lowest at risk):
| 1. Bangladesh | 8. Nepal | 15. Taiwan |
| 2. Pakistan | 9. Thailand | 16. South Korea |
| 3. Cambodia | 10. Philippines | 17. Hong Kong |
| 4. Indonesia | 11. Sri Lanka | 18. Singapore |
| 5. Mongolia | 12. China | 19. Australia |
| 6. Myanmar | 13. India | 20. New Zealand |
| 7. Vietnam | 14. Myanmar | 21. Japan |
Ransomware Attacks on the Rise
Ransomware is one of the most infamous malware families in 2017. In the first half of this year, two waves of ransomware attacks, WannaCrypt and Petya, exploited vulnerabilities in outdated Windows operating systems worldwide and disabled thousands of devices by illegitimately restricting access to data through encryption. This not only disrupted individuals’ daily lives but also crippled many enterprises’ operations.
The attacks have been disproportionately concentrated in Europe, while most of the Asia markets have not been too heavily impacted. In fact, Japan and China have been listed as the two countries with the lowest ransomware encounter rate. One of the few exceptions in the region is South Korea, which has had the second highest ransomware occurrences worldwide.
Attackers evaluate several factors when determining what regions to target, such as a country’s GDP, the average age of computer users and available payment methods. The region’s language can also be a key contributing factor as a successful attack often depends on an attacker’s ability to personalize a message to convince a user to execute the malicious file.
Globally, Win32/Spora has rapidly become one of the most widespread ransomware families and it was the most commonly encountered ransomware family in March 2017. Spora encrypts files with several popular extensions, including .doc, .docx, .jpg, .pdf, .xls, .xlsx, and .zip. This ransomware also has worm capability, making it capable of spreading to other computers in a network.
Cloud Accounts and Services Under Cyber Siege
As cloud migration increases, the cloud has become the central data hub for a majority of organizations. This also translates into more valuable data and digital assets being stored the cloud, making it a growing target for cybercriminals.
The SIR found a 300 percent increase in global attacks against consumer and enterprise accounts managed in the cloud over the past year. Meanwhile, the number of logins attempted from malicious IP addresses has increased by 44 percent year over the year.
A large majority of these compromises are the result of weak, guessable passwords, and poor password management. Targeted phishing attacks and breaches of third-party services are also major problems. As the frequency and sophistication of attacks on user accounts in the cloud accelerates, there is an increased emphasis on the need to move beyond passwords for authentication.
Building Trust in the Digital World by Strengthening Cybersecurity Posture
As the threat landscape continues to evolve and grow, organizations need to ensure they have a solid cybersecurity architecture and robust cyber hygiene best practices. This will enable them to better protect their digital environment, detect threats and respond to attacks.
Here are four best practices that individuals and organizations can consider to minimize their cyber risk exposures and stay resilient in an everchanging threat landscape.
• Do not work in public Wi-Fi hotspots where attackers could eavesdrop on digital communications, capture logins and passwords, and access personal data.
• Regularly update the operating system and other software programs to ensure the latest patches are installed. This reduces the risk of vulnerability exploitation. Users should also install the most recent release of Windows 10 to take advantage of its improved hardening and security mitigations.
• Reduce the risk of credential compromise by educating users on why they should avoid simple passwords and enforcing multi-factor authentication methods. For example, the Azure Multi-Factor Authentication (MFA) provides organizations with a two-step verification solution that helps safeguard access to data and applications. It also meets user demand for a simple sign-in process by delivering strong authentication via a range of easy verification options.
• Enforce security policies that control access to sensitive data and limit corporate network access to appropriate users, locations, devices, and operating systems. For example, Microsoft Azure Active Directory Identity Protection enables enterprises to configure risk-based policies to automatically protect the identities across their organization. These policies can automatically block the user without the proper authorization or offer suggestions that include password resets and multi-factor authentication enforcement.
“In today’s digital age, security cannot be an afterthought. It must be “built-in”, all-inclusive and intelligent,” said Keshav. “The comprehensive threat intelligence that we provide with our SIR as well as advanced security solutions and best IT hygiene practices will all play a critical role in integrating cybersecurity into an organization’s DNA.
“By making security a top priority, we can build greater trust in technology and enable digital transformation to reach its fullest potential and fulfil its grandest ambitions.”
Resources like the SIR are just one aspect of the Microsoft comprehensive approach to security – including a holistic platform, unique intelligence and broad partnerships – which is critical to enabling the digital transformation of leading organizations in Asia. You can check out the Microsoft Secure website to find out more.
To download and learn more about the Microsoft Security Intelligence Report findings, visit www.microsoft.com/sir
ALSO READ: New Microsoft security report stresses online identity protection
For more information, please visit the official Microsoft Secure blog post, as well as the infographic below: